强网杯s7 强网先锋三道简单的re题wp
强网杯,哎…….我还是太菜了!
下面这些题还算是可以出的,就一起写了,后面的那些比较难的题我就慢慢复现吧!
ps:很抱歉之前的wp写的有点乱,这边重新整理一下
Babyre【强网先锋】
(xtea魔改)
先通过字符串定位到main函数
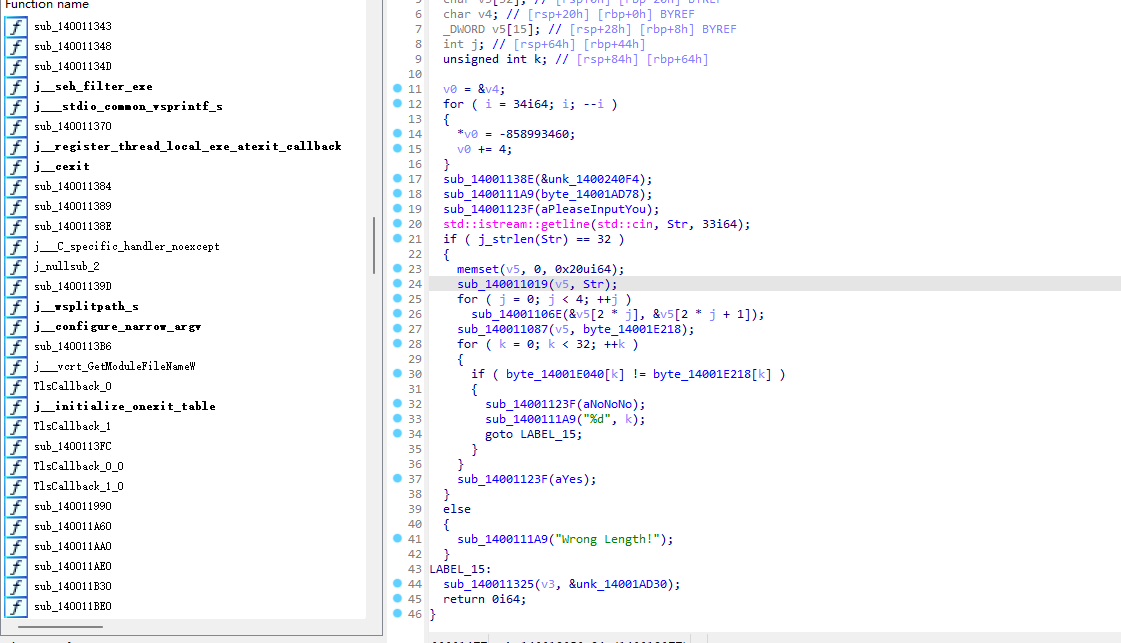
1 | for ( j = 0; j < 4; ++j ) |
有一个四次循环的调用函数,并且传入的参数是v5,v5之前有和input一起调用的函数,可能v5就是cmp的input
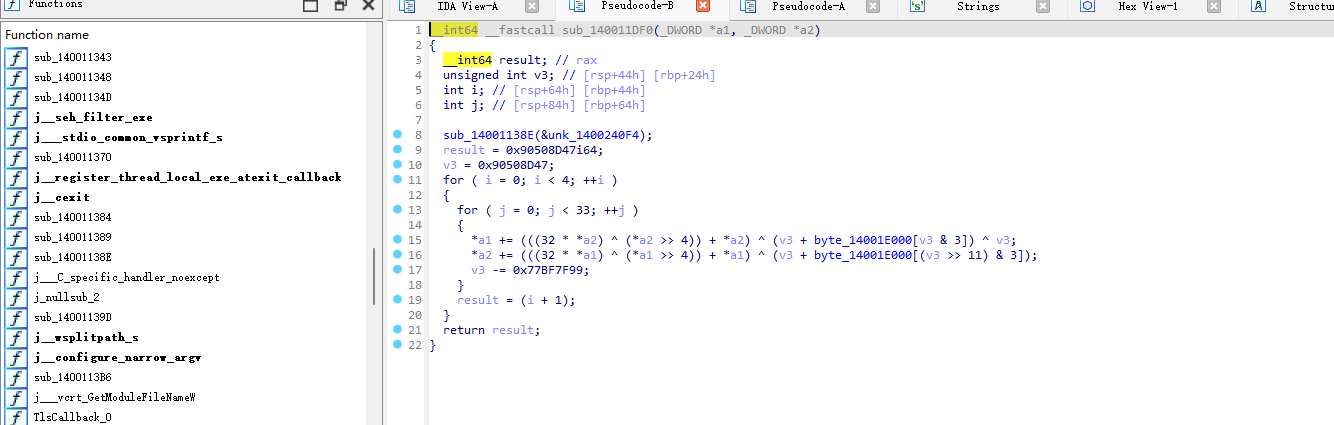
里面是一个xtea byte_14001E000里面的key也就是内容存放的地方:
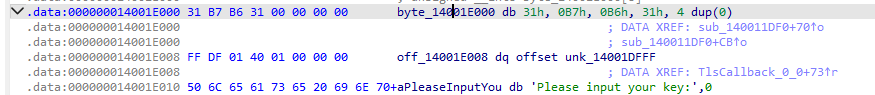
但是经过代入脚本发现这个key有问题,可能是在函数运行的时候对key做了手脚
动调看看 因为程序在直接动调的时候怪怪的,所以就通过载入进程的方式调,然后找到xtea的位置进行查看,找到了key:
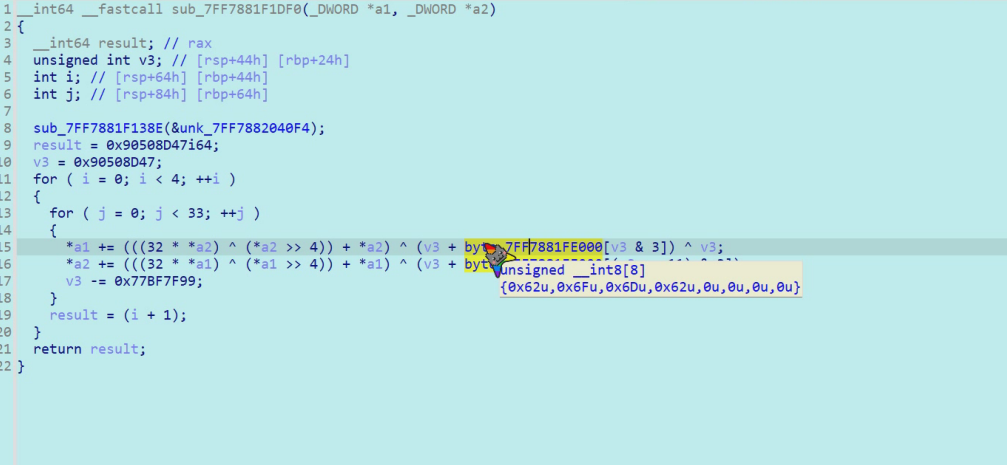
del和sum也找到了,在图里,密文如下
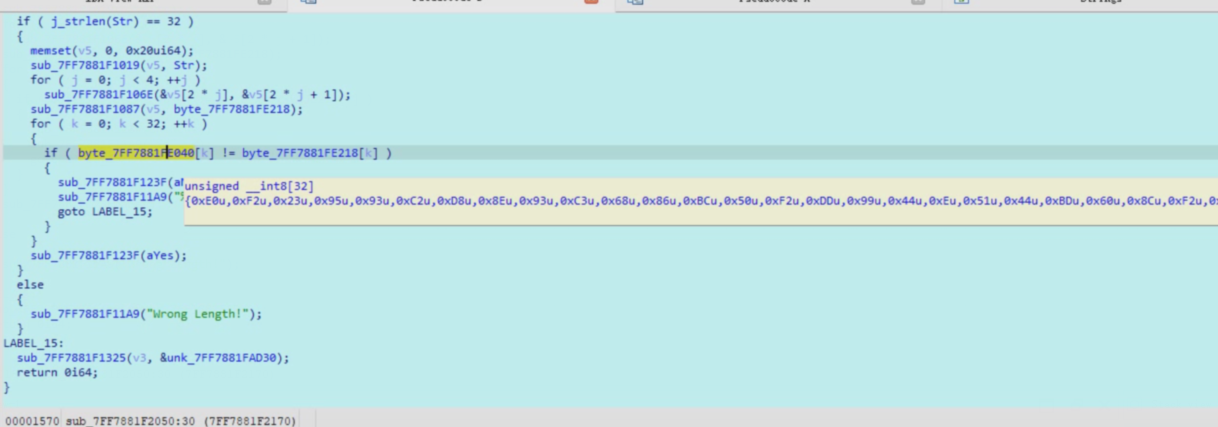
并且这个加密的调用方式也是四个一循环,然后2i和2i+1的方式进行加密,解密也这样就可以了 最终脚本如下:
1 | #include <stdio.h> |
flag{W31com3_2_Th3_QwbS7_4nd_H4v3_Fun}
ezre【强网先锋】
(ollvm控制流平坦化、base来回加解密、判断动态调试执行函数)
都是o简单的llvm控制流平坦化,先用脚本都把ollvm混淆去掉
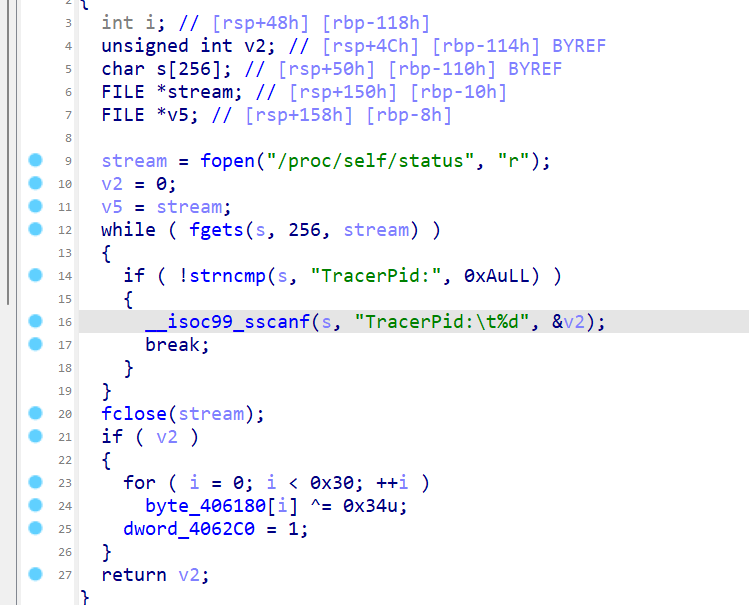
这个函数是一个判断有没有进入调试状态,如果进入了调试状态,那么就会给
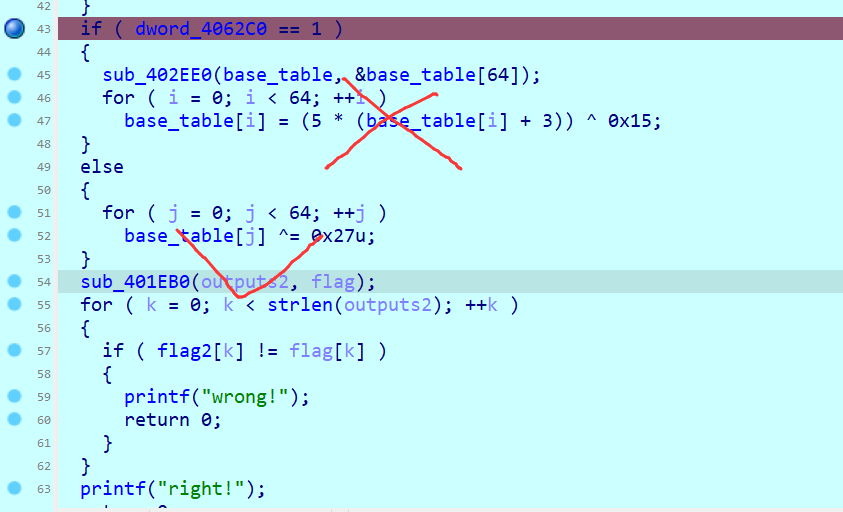
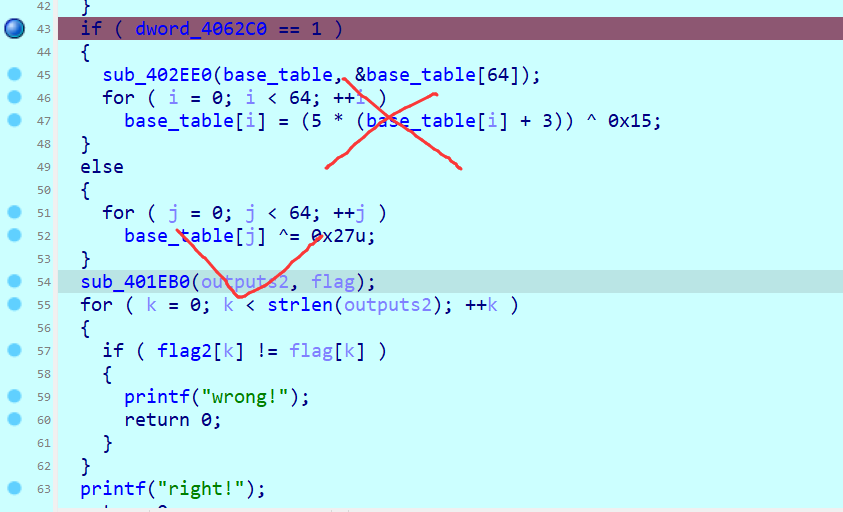
dword_4062C0 = 1 这个参数在后面也有在被用到
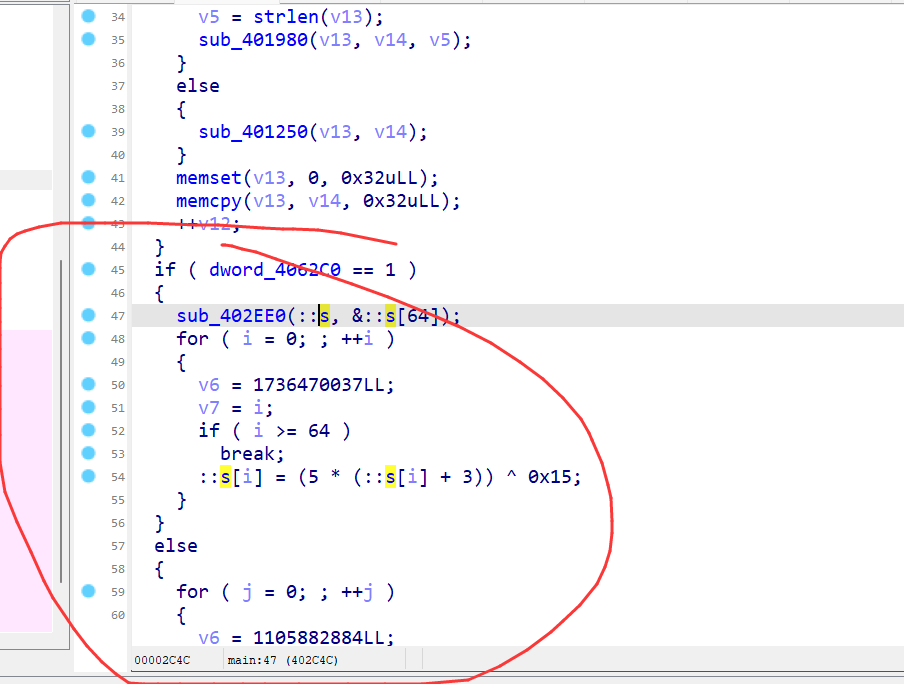
在后面进行操作,如果是调试的话就会对密文进行一个异或操作,以及改了很多次的码表,所以调试的话会和非调试的时候运行的代码不一样
然后就是一系列的base加解密
加密过程:
循环之前:
l+USN4J5Rfj0TaVOcnzXiPGZIBpoAExuQtHyKD692hwmqe7/Mgk8v1sdCW3bYFLr
enc
0
FGseVD3ibtHWR1czhLnUfJK6SEZ2OyPAIpQoqgY0w49u+7rad5CxljMXvNTBkm/8
dec
1
Hc0xwuZmy3DpQnSgj2LhUtrlVvNYks+BX/MOoETaKqR4eb9WF8ICGzf6id1P75JA
enc
2
pnHQwlAveo4DhGg1jE3SsIqJ2mrzxCiNb+Mf0YVd5L8c97/WkOTtuKFZyRBUPX6a
dec
3
plxXOZtaiUneJIhk7qSYEjD1Km94o0FTu52VQgNL3vCBH8zsA/b+dycGPRMwWfr6
enc
然后通过手动计算出basetable的数值,即上面的字符串异或0x27
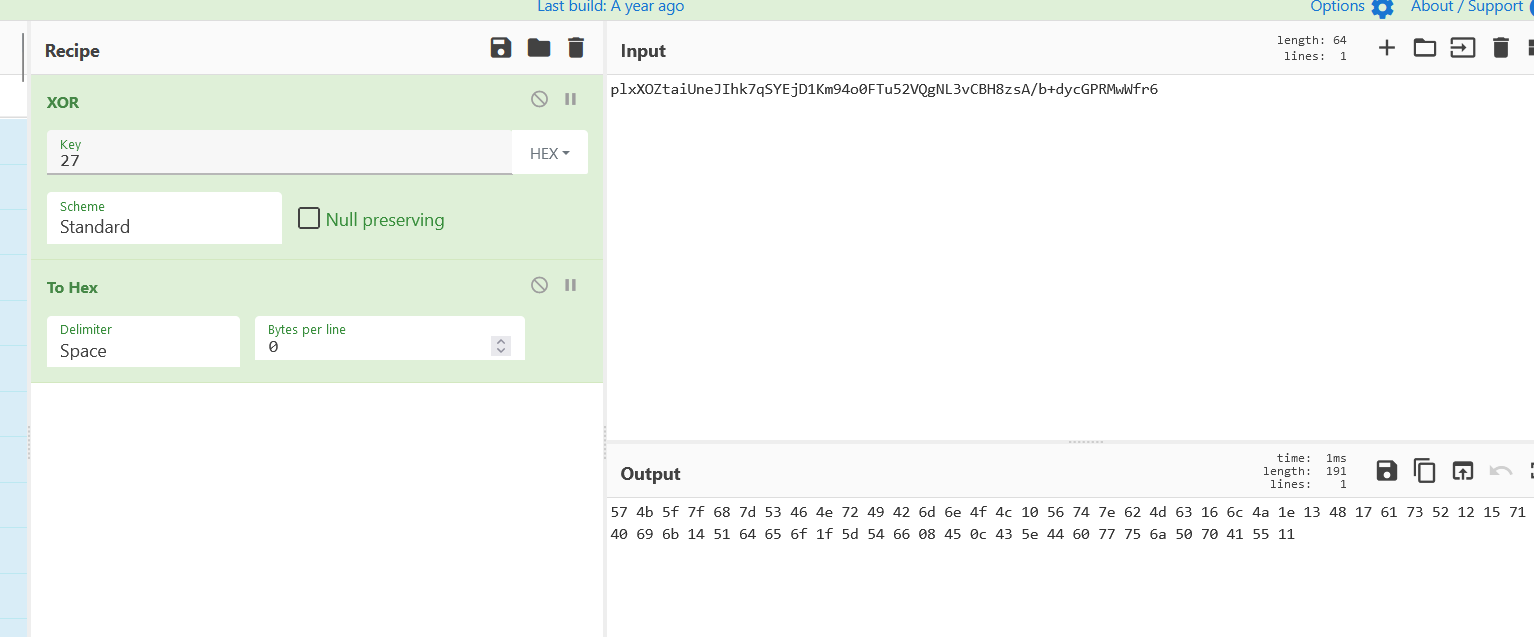
拿到新的table
1 | #include <stdio.h> |
通过c代码进行的加密复现,并且拿到正常运行情况下的v3和v5 然后python的解密脚本:
1 | def xor_array_backward(arr): |
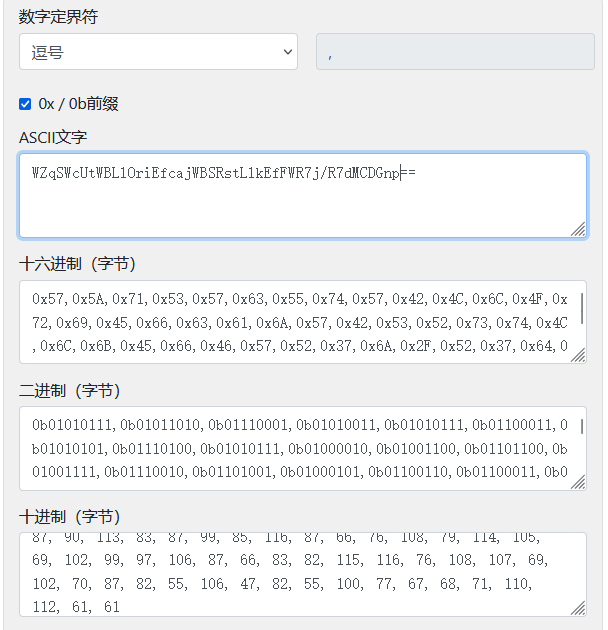
然后拿到赛博厨子上逆一下上面的base
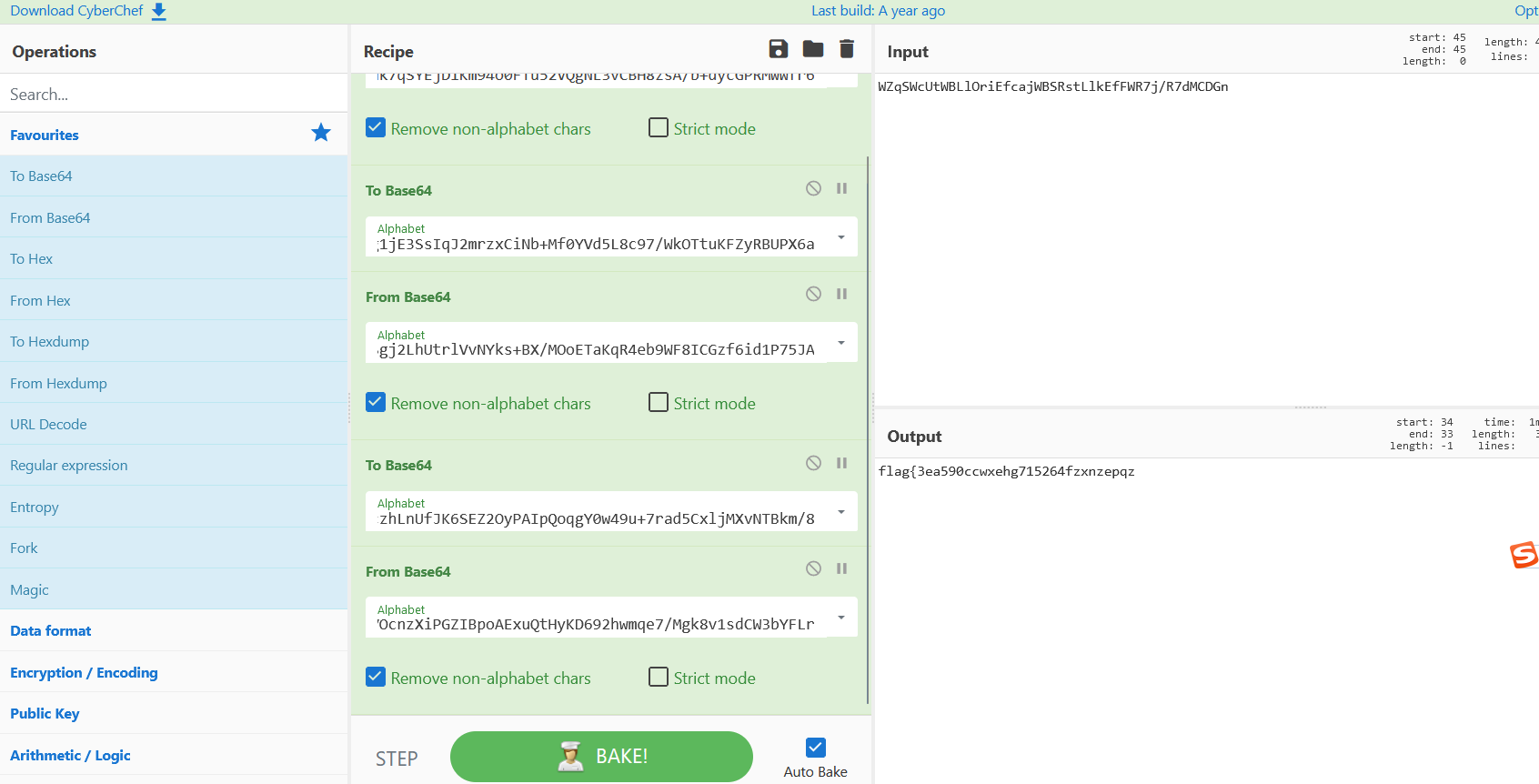
拿到flag
去ollvm混淆
首先配置defalt环境,然后再去用指令 python defalt.py -f ezre –addr 0x0000(地址)
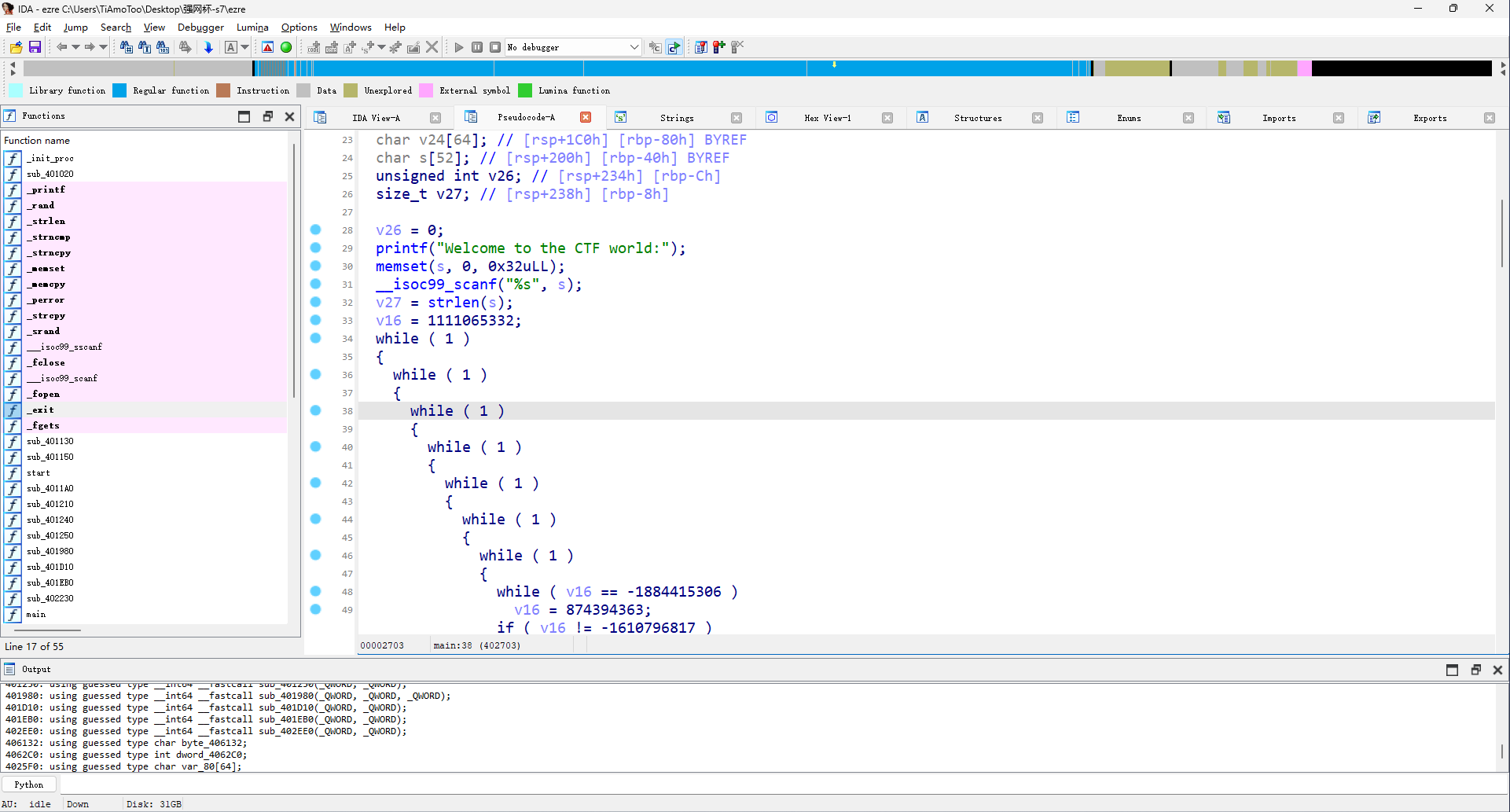
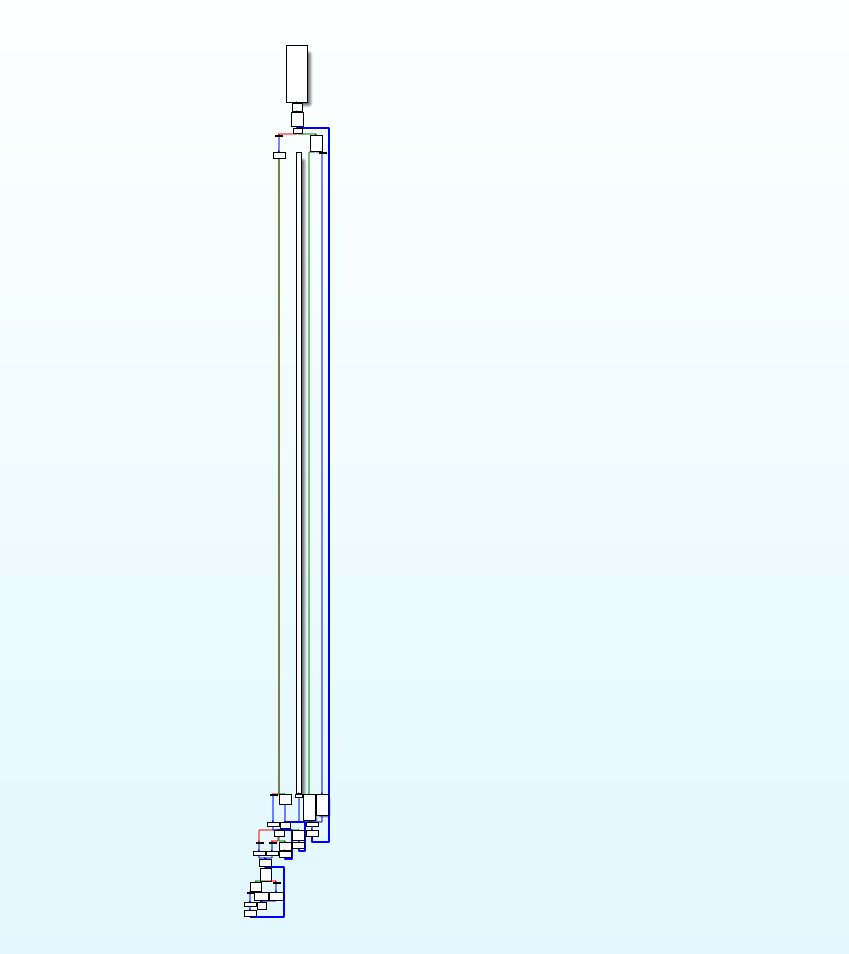
这是去除之前的main函数,哎,一眼ollvm
流程图
然后通过汇编,定位到这个函数的入口的posh点
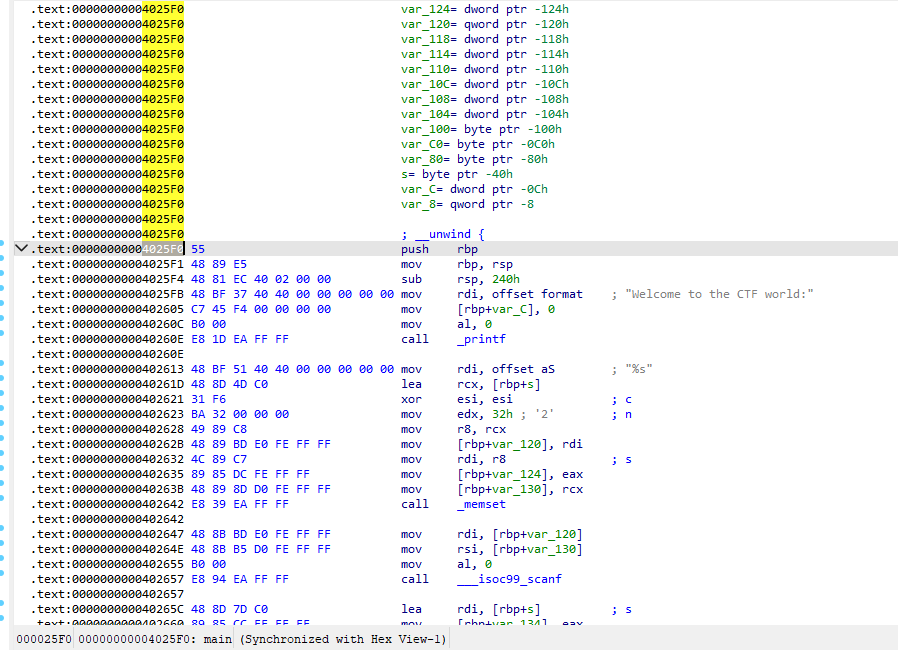
这里就是4025F0
指令:python deflat.py -f ezre –addr 0x4025f0(其他地方的类似)
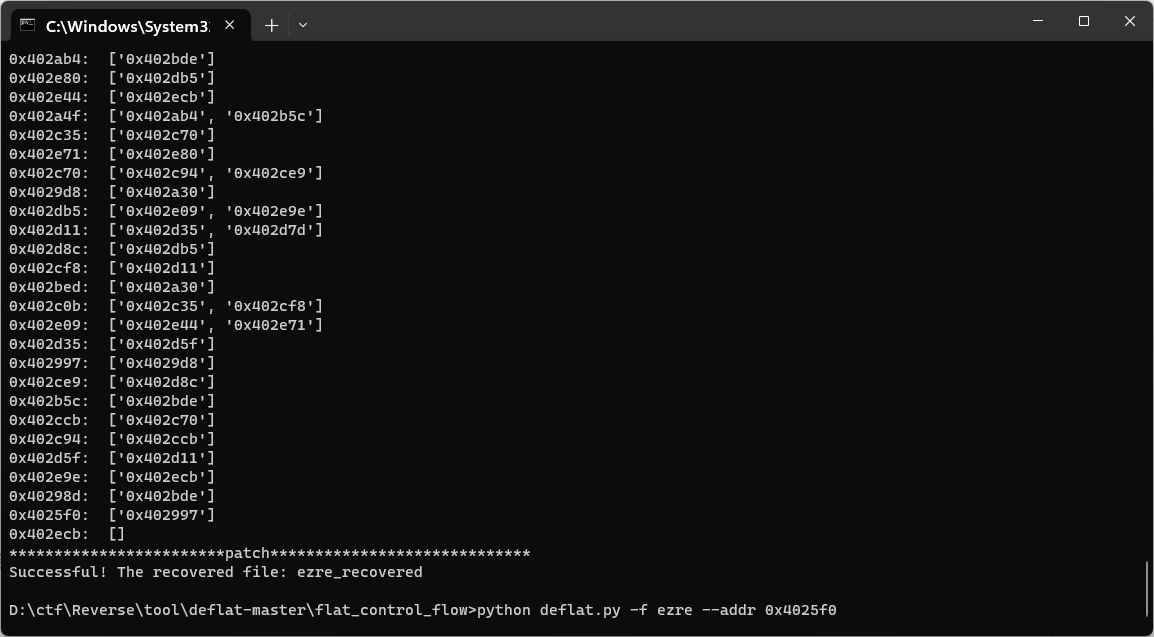
逆完之后的控制流就恢复正常了
代码也是差不多可以看了!
代码分析
都是简单的llvm控制流平坦化,先用脚本都把ollvm混淆去掉
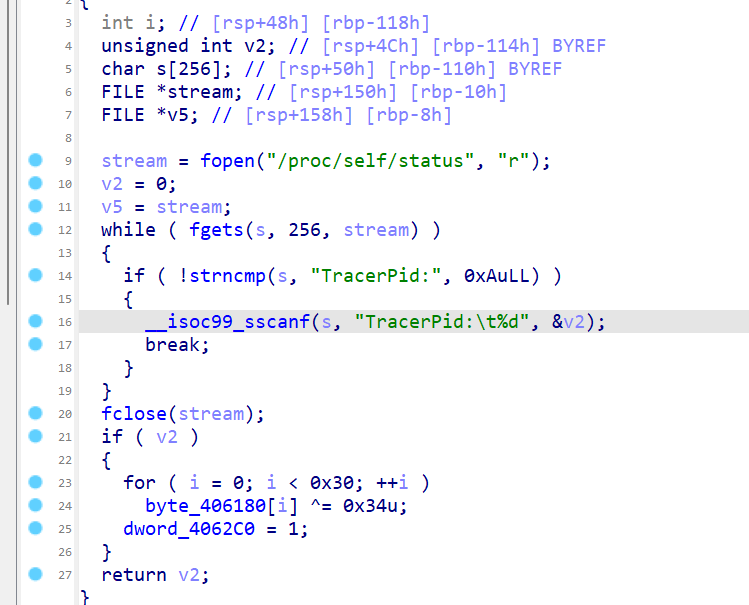
这个函数是一个判断有没有进入调试状态,如果进入了调试状态,那么就会给
dword_4062C0 = 1 这个参数在后面也有在被用到
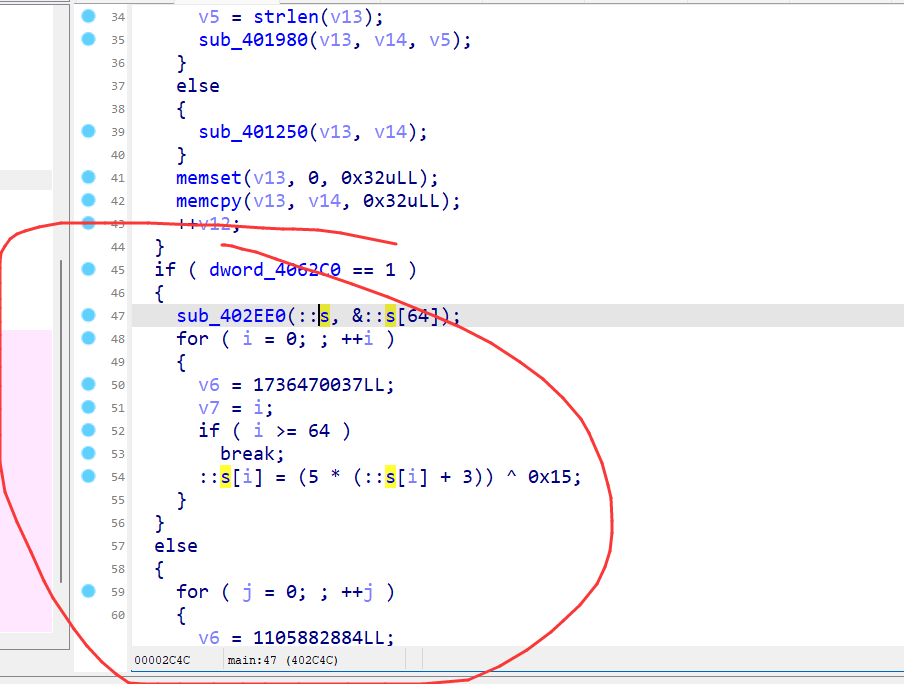
在后面进行操作,如果是调试的话就会对密文进行一个异或操作,以及改了很多次的码表,所以调试的话会和非调试的时候运行的代码不一样
然后就是一系列的base加解密
加密过程:
循环之前:
l+USN4J5Rfj0TaVOcnzXiPGZIBpoAExuQtHyKD692hwmqe7/Mgk8v1sdCW3bYFLr
enc
0
FGseVD3ibtHWR1czhLnUfJK6SEZ2OyPAIpQoqgY0w49u+7rad5CxljMXvNTBkm/8
dec
1
Hc0xwuZmy3DpQnSgj2LhUtrlVvNYks+BX/MOoETaKqR4eb9WF8ICGzf6id1P75JA
enc
2
pnHQwlAveo4DhGg1jE3SsIqJ2mrzxCiNb+Mf0YVd5L8c97/WkOTtuKFZyRBUPX6a
dec
3
plxXOZtaiUneJIhk7qSYEjD1Km94o0FTu52VQgNL3vCBH8zsA/b+dycGPRMwWfr6
enc
然后通过手动计算出basetable的数值,即上面的字符串异或0x27
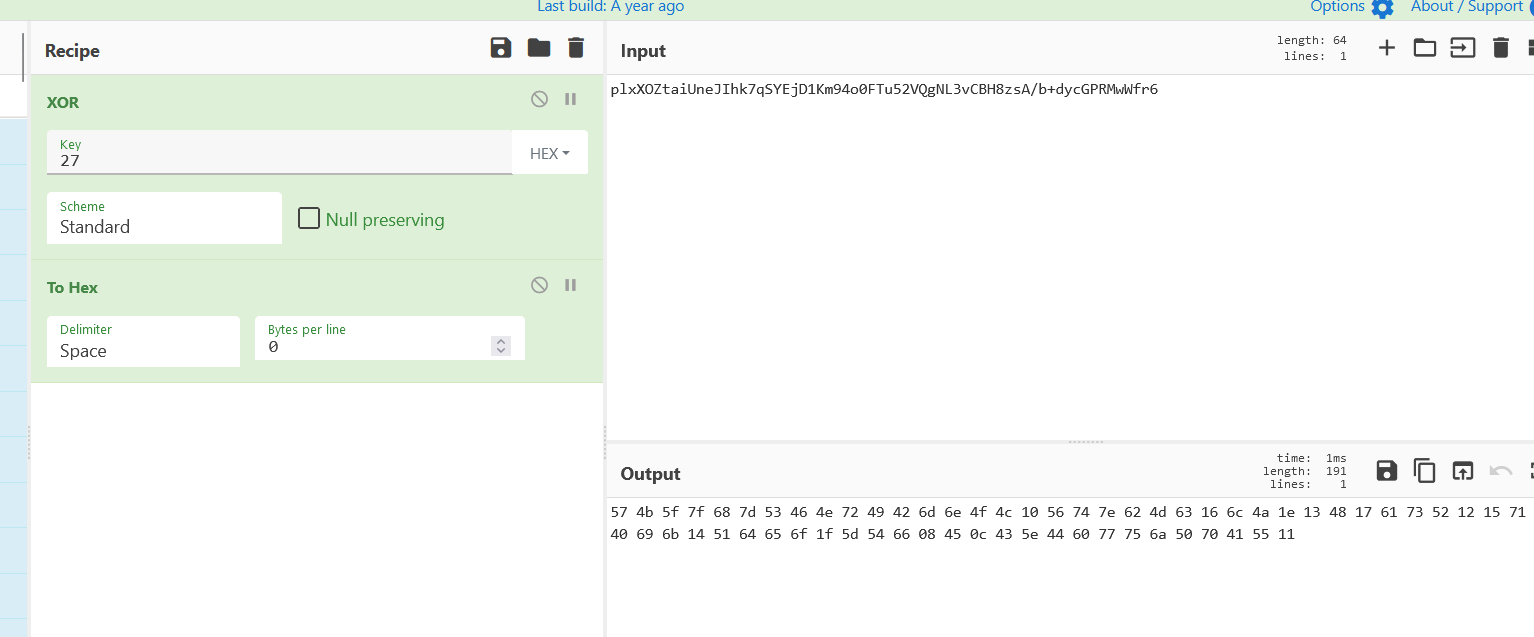
拿到新的table
1 |
|
通过c代码进行的加密复现,并且拿到正常运行情况下的v3和v5 然后python的解密脚本:
1 | def xor_array_backward(arr): |
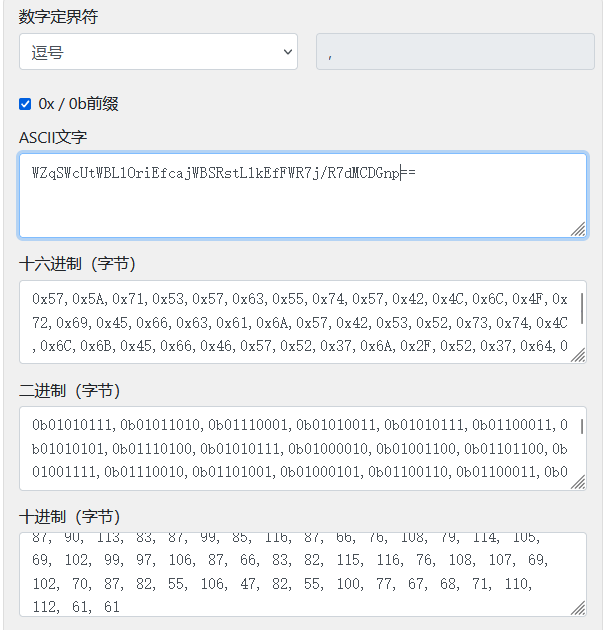
然后拿到赛博厨子上逆一下上面的base
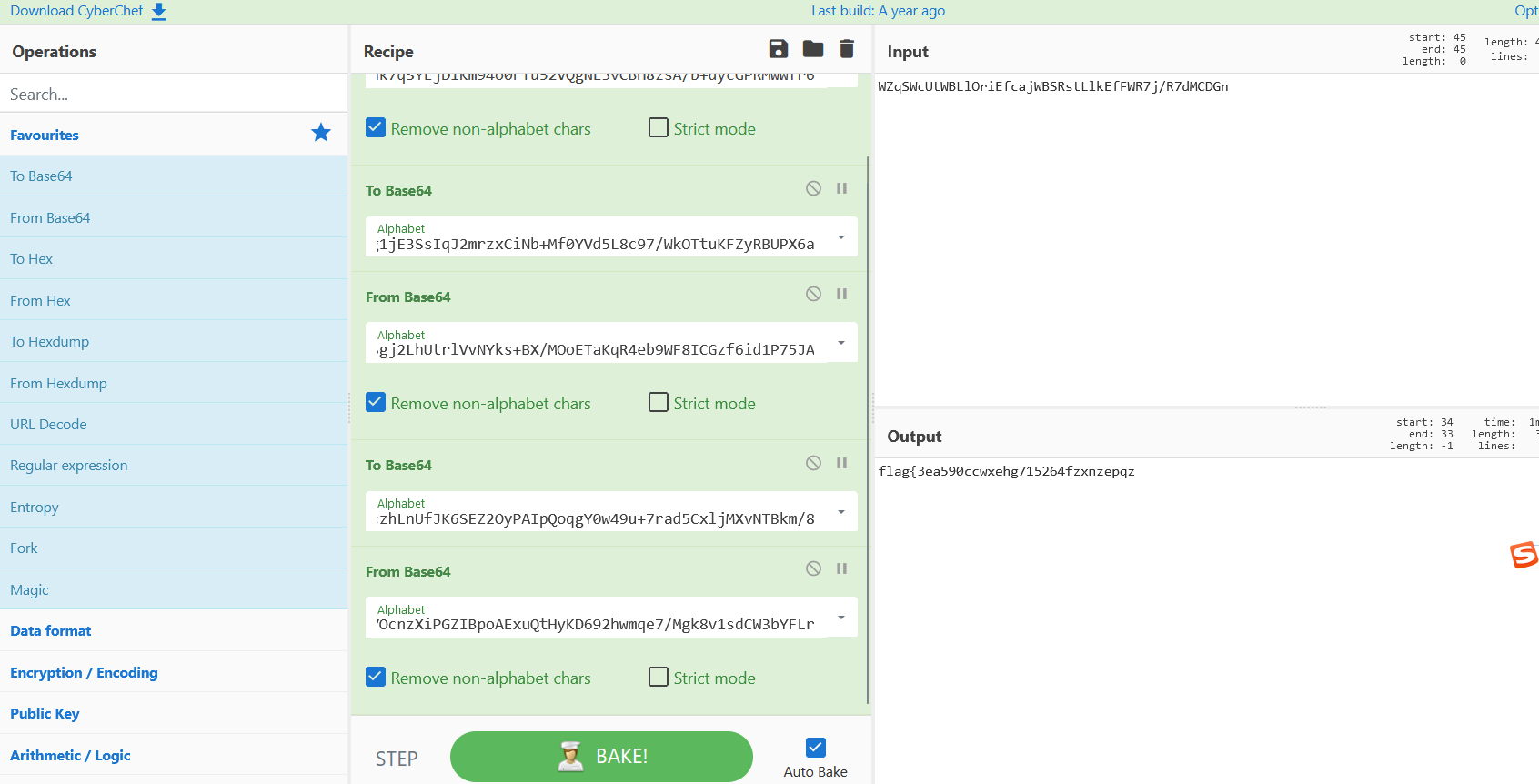
拿到flag
ezre【强网杯】
这题又是ollvm混淆,而且控制流更加离谱了
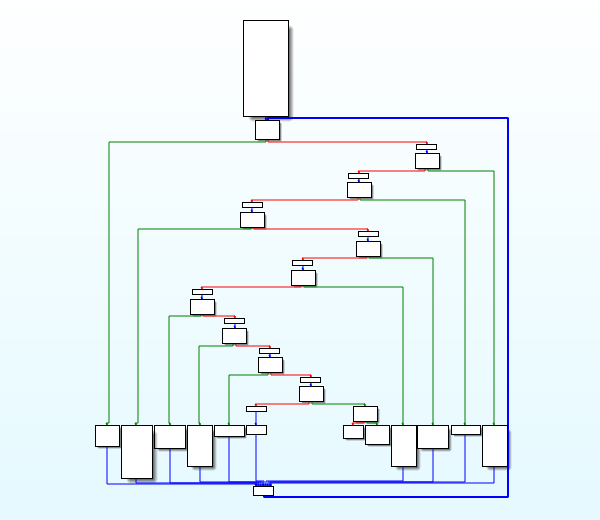
一个是main函数的比较简单的混淆,然后再通过字符串索引,找到了一个更混乱的控制流
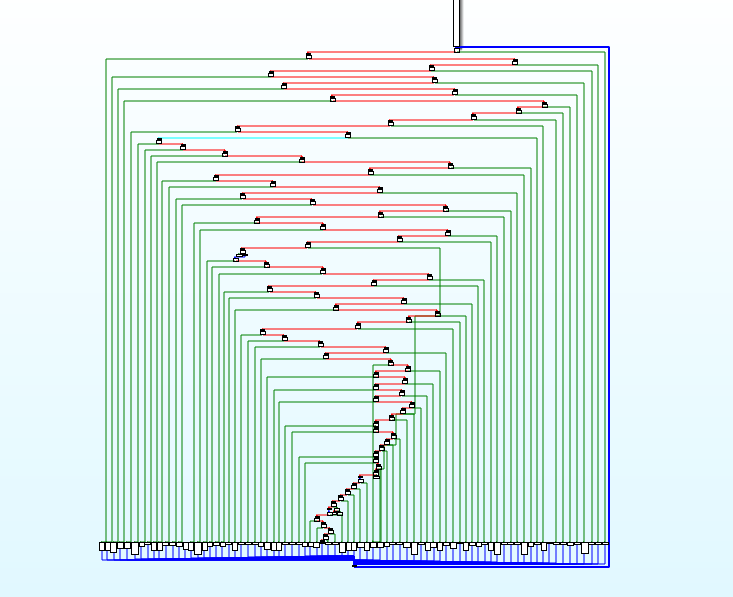
好玩,爱玩!
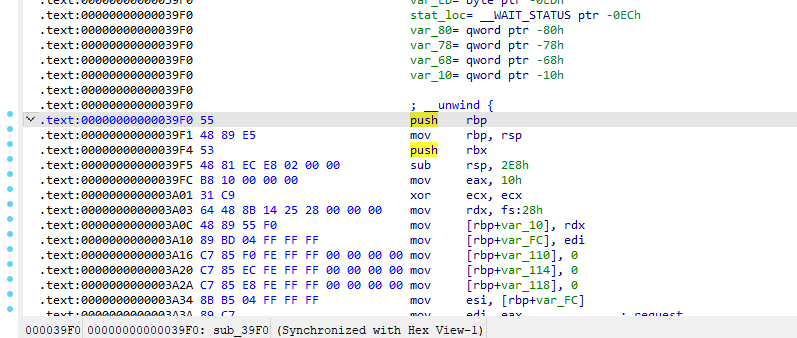
D810插件用起来怪怪的而且我个人编译起来特别卡(特别是动调的时候,非常卡)
还得是defalt,找到相对应的函数入口地址然后直接用angr跑一下了
但是这里的话是39F0,试过去ollvm但是没成功,问了问大佬才知道,原来是有偏移,一般来说前面都会有40为基地址,所以直接去去掉0x4039f0就可以了
python deflat.py -f chall –addr 0x4039F0
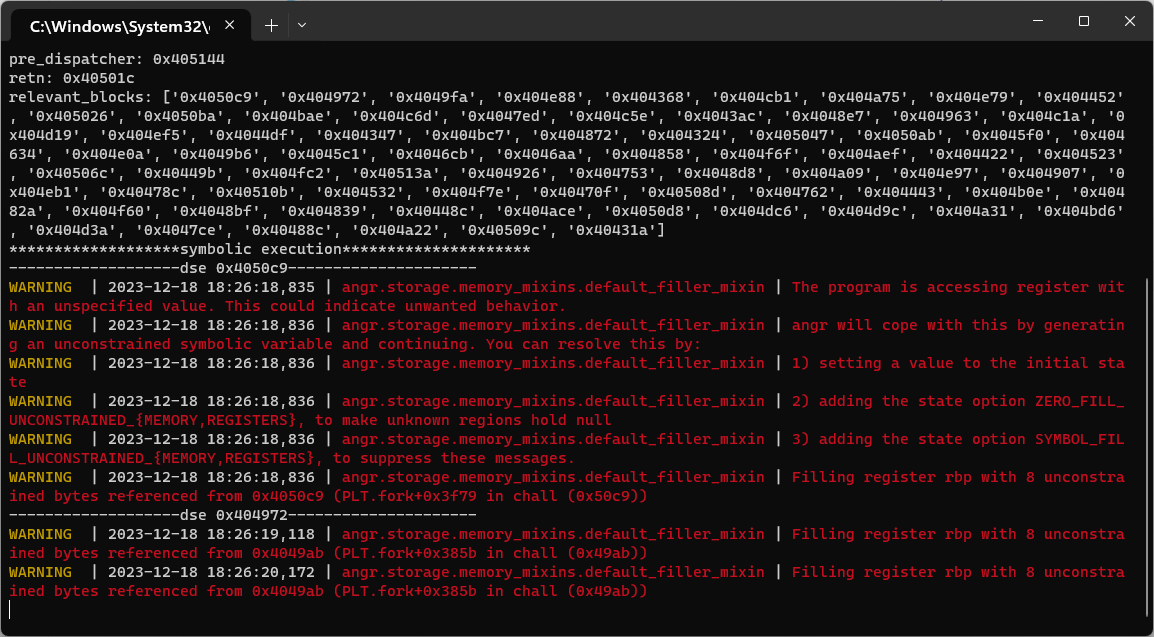
程序的控制流很乱,得跑上一段时间
最喜欢看到的!
main函数也顺便去一下
python deflat.py -f chall –addr 0x405290
还有一个地方,反正有混淆就去就行了
python deflat.py -f chall –addr 0x403580
恢复了
但是巡视一圈,发现没啥加密,就有一个SM4加密
这里有一个好玩的地方:我是用defalt和D810去混淆,结果给我的结果不一样,哎,好像defalt的结果有点问题,但是好在影响不是很大:
defalt:
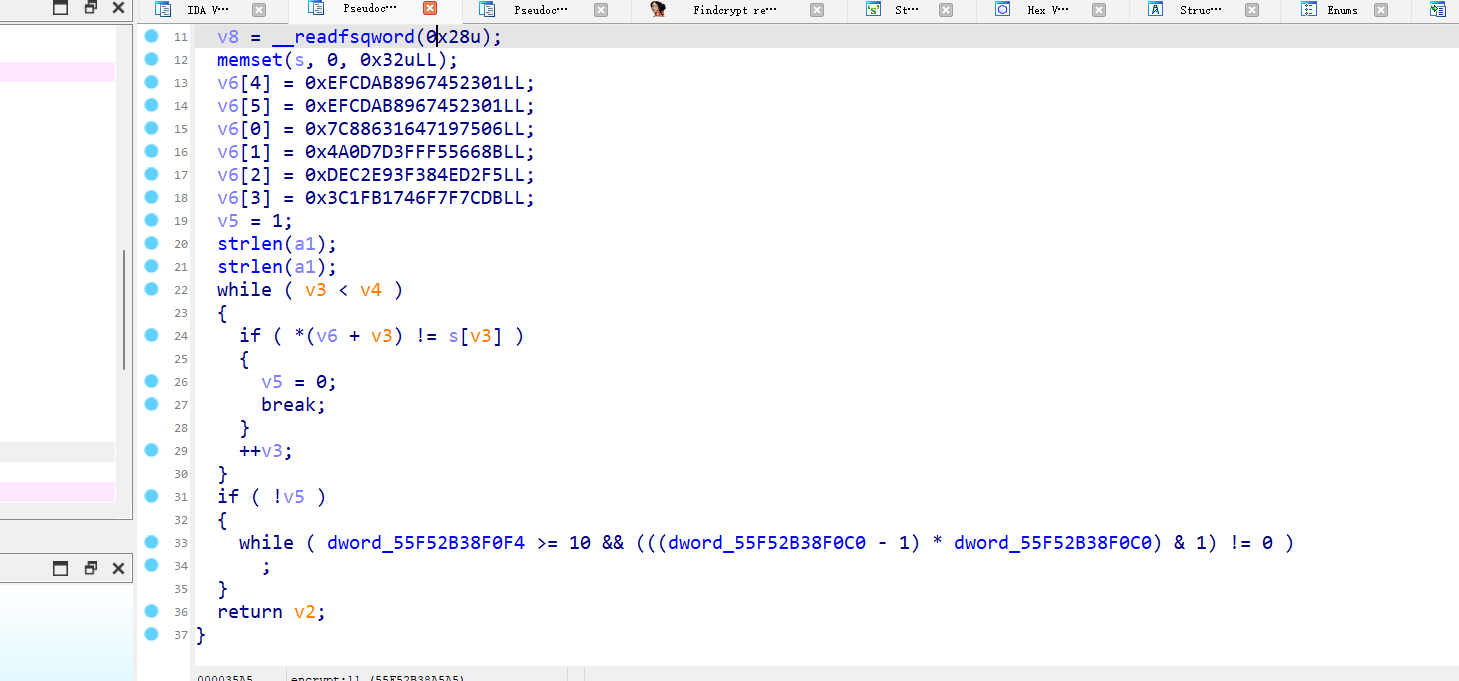
D810:
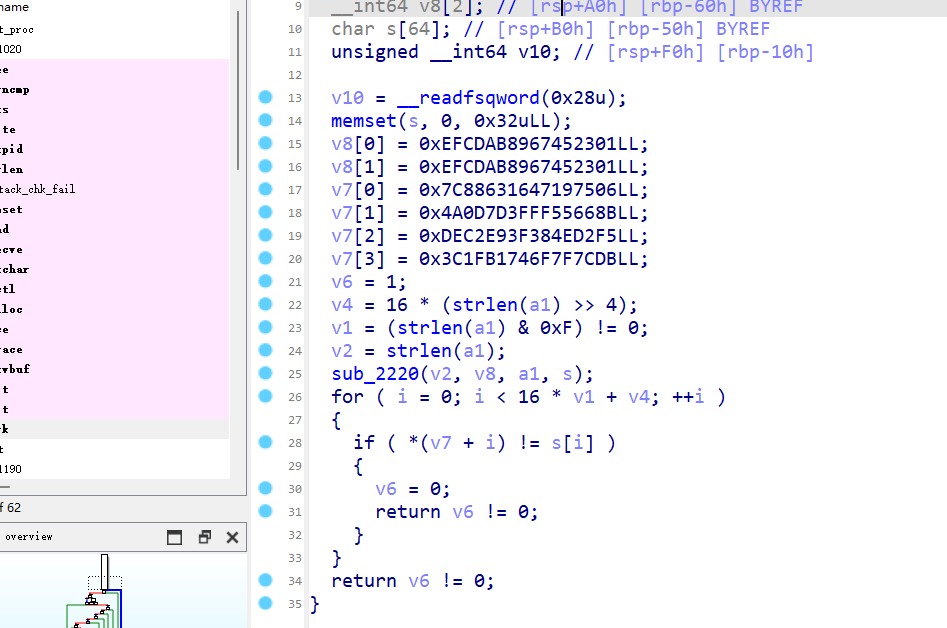
还得是b810,就按照D810的来分析了
SM4国产加密的特长,国产加密yyds
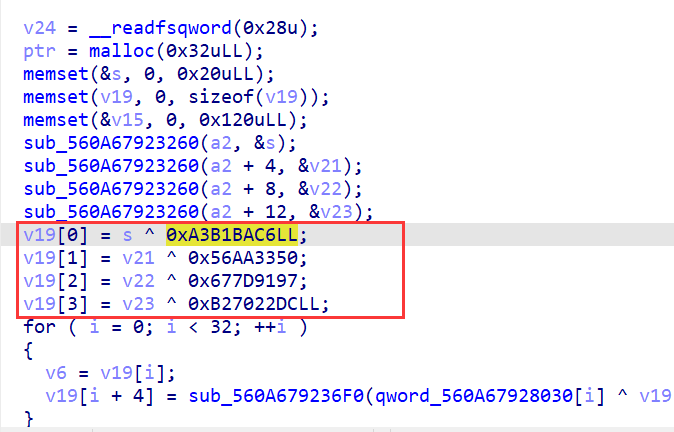
v8很明显是秘钥,v7是密文,提取出来直接拿到赛博厨子直接梭哈
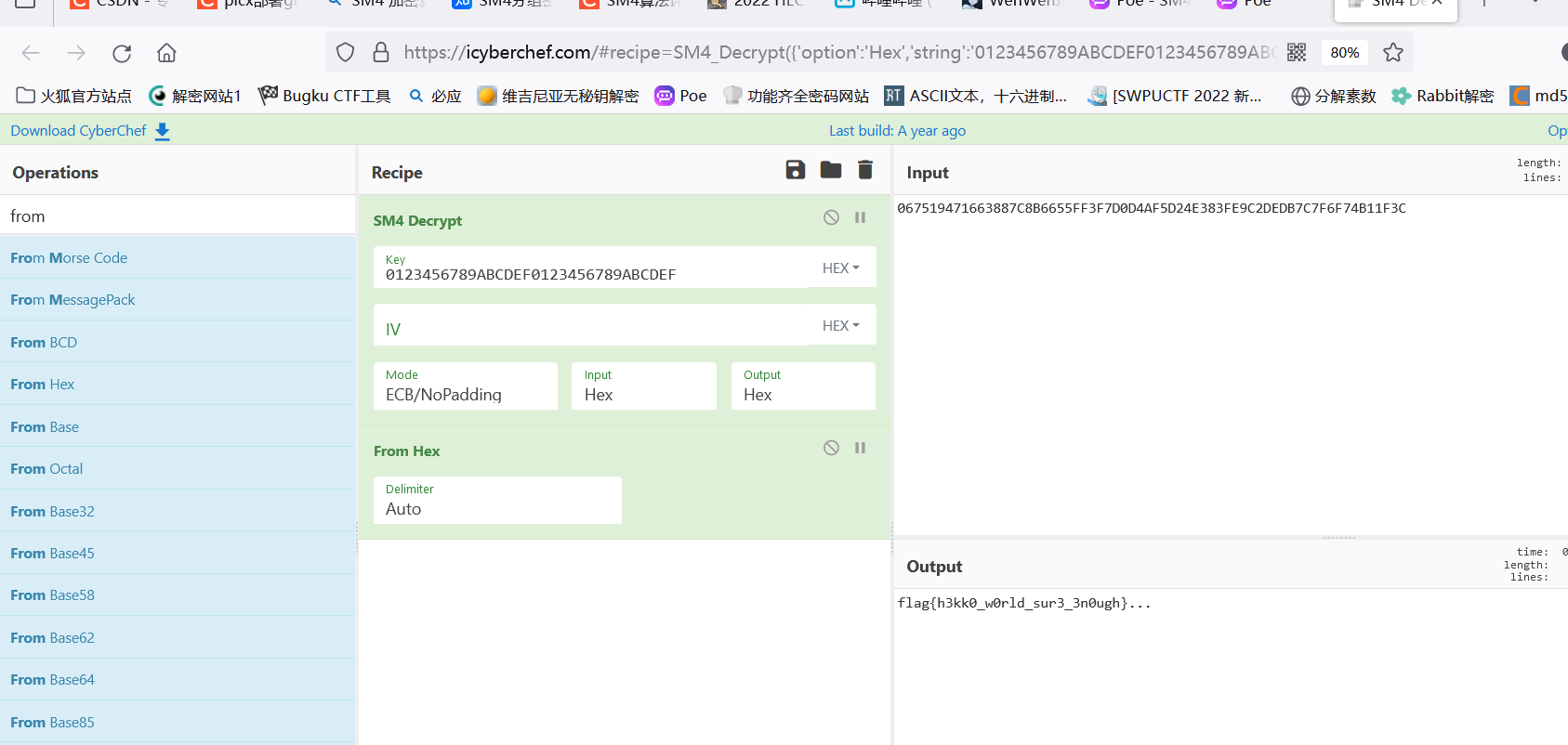
半自动化转化端绪脚本:
顺便贴上一个端绪转化的半自动化脚本:
1 | def endian_conversion(hex_value): |
要不然一个一个转的话真的累了!